Simplified Information Security Risks
Varutra SOC & Global Threat Management Services delivers real-time Threat, Log monitoring and Alert analysis to minimize any impact on business operations and reduce overall security risks to help organizations improve business continuity and enhance the efficiency of security operations.
Recent Cyber attacks are getting advanced, targeted and aggressive, every day and every single minute. Our SOC & Global Threat Management Services provides continuous protection round the clock in a rapidly changing digital world of known as well as unknown cyber threats.
Our Statistics at Peak Hours!
Key Service Offerings
SOC as a Service
Cyber Security is a complex area and so is managing it.
At Varutra, we enable information security via offering a comprehensive SOC-as-a-Service under our SOC & Global Threat Management Services.
Our real time SOC monitoring service ensures that we protects critical devices and data they transit/store and provide continuous security monitoring.
Benefits
- 24x7x365 Real time Security Alert Monitoring
- Highly Customizable Packages
- Onsite as well as Offsite Model
- Enhanced Security Posture
- Cost Effective Solution
SOC-as-a-Service Features
24x7x365 Monitoring across corporate network
Intelligent security Threat Monitoring and Analysis
Managed IDS/IPS and Firewall administration
Periodic SIEM finetuning and Optimization
Real time Ticketing via VMSD application and via Customer Ticketing Portal
Managed Antivirus/DLP Monitoring and administration
Dedicated Technical Account Manager
Access to Cyber Threat Post Security Advisories
Facilitate Compliance and Regulatory Standards
Threat Intelligence & Dark Web Scanning
Traditional Security is not always enough in these days of 0 days and sophisticated ransomware attacks.
Our Threat Intelligence feeds ensure that we proactively monitor our customer environments and the external threat landscape to detect and mitigate targeted cyberattacks.
Our team has the capability to turn intelligence feeds updates into actionable mitigation approaches to help customers respond to threats relevant to their business.
Benefits
- Monitor, Detect and Respond to Insider Threats
- Clear visibility to focus on protecting sensitive data
- Leverage on Open Source as well as Commercial Threat Intelligence feeds
- Continuous monitoring of threat landscape to report on threats outside of customer perimeter
Threat Intelligence & Analytics Features
Darknet Cyber Threat
Surveillance
Malware and IOCs Threat
Hunting
Threat Correlation via Threat Feeds against SIEM Use Cases
Strategic Threat Hunting preventing Cyber Espionage
Proactive Detection and Security Incidents Reporting
Cyber Attacks and e-Crime
intelligence
Insider Threat Surveillance on
Deep web
Leverages Commercial and OSINT
Data Lakes
Digital Brand Protection and Brand Monitoring
Digital Forensics & Security Incident Response
In spite of putting multiple effort’s in threat prevention and detection, the unavoidable is bound to happen and no organization is exception to it.
Our Digital Forensics & Investigation and Cyber Incidence Response help our customers to proactively retort to and recover from a persistent cyber attack.
Our Security Incident Response competencies support customers in overcoming short to long term consequences of a cyber incident.
Benefits
- Supports Organizations Crisis Management Program
- Aligned with Organizations Cyber Security Program implementation
- Proactive, business-focused incident response strategies tailored to organizational goals
Digital Forensics & Security Incident Response Features
Endpoint Forensics and Protection
Services
Web Defacement and
Breach Analysis
Data Breaches and Data
Leakages Investigation
Proactive Incident Prioritization
and Remediation
Surface Web and Darknet Scanning for
Data Leakages
Assist in setting up a Computer Security Incident Response Team (CSIRT)
Round the clock Incident Response Center for Realtime Security Monitoring
On-demand Investigation tailored to meet Business needs
Cybercrime and Cyber Awareness
Training
Security Advisory Services
Our highly sophisticated Security Advisory Services enable enterprises to stay up to date on latest security vulnerabilities being disclosed and mitigate open security risks before the bad guys do, by deploying security patches and system hardening.
In recent days of Zero day and Ransomware attacks, organizations should opt for security advisory services in return of guaranteed efforts against protecting the data and critical information.
Benefits
- Security Advisories against customer specific Technology mapping
- Assess Real-time risks and define business aligned patch management strategies
- Real world, easy and actionable recommendations to swiftly mitigate threats
Security Advisories Features
OSINT and Commercial data sources to Monitor Threat alerts
Realtime Access to Cyber Threat Post Security Dashboard
Tailored Advisories and Recommendations to enhance cybersecurity controls
Customer Business Technology mapping and Vendor neutral advisory consulting
Identifies areas of High risks and mitigate with minimal IT efforts
Design and Implement Cyber Defense Blueprint to deliver best possible protection
Threat Prioritization and Recommendations to eliminate Cyber risks
Deep Insights into Threat Actors, Attack patterns and Attack Tactics
Act as a Principal extension to customer IT Team
Vulnerability & Threat Management
Organizations face challenges in efficiently tracking and managing the remediation of a large number of security vulnerabilities.
Our team helps managing the entire Vulnerability Management life cycle program from identifying the critical assets, to managing execution of the assessment to remediation, and to reporting.
Benefits
- Customized to client-owned vulnerability scanner solution or wholly owned and managed by Varutra
- 24×7 support schedule to curb recent threats and their impact on organizational assets
- Aligned with our Threat Intelligence services and Security Advisory services to combat known / unknown cyber threats
- Saving on customer administrative overhead
Vulnerability & Threat Management Features
Asset Discovery, Prioritization and Evaluation
Proactive Mitigation of Residual Vulnerabilities
Focused towards Cyber
Resilience
Effective Vulnerability Scanning across Internal, External Assets
Transparency via Actionable Reports for Immediate Actions
Customized Dashboards and Automation enabled protection
Real Risk Exposure and Impact Analysis
Assistance in Vulnerabilities Identification and Remediation
Cost Effective models to Optimize Vulnerability Management program
Security Assessments
Our tailored security assessment programs, covering the entire threat landscape right from penetration testing to security awareness training, is delivered via our certified security professionals offering their expertise towards customer security.
Our team is committed in helping our customers achieve the desired cyber safe profile and tightened security posture.
Benefits
- Comprehensive & in-depth Security Assessments
- Comprises of Web, Mobile & Network Security
- Effective ROI & Time Bound Exercises
- Actionable Deliverables Focusing on Remediation
- Enhanced Security Posture
Security Assessments Activities Features
Network Vulnerability Assessment and Penetration Testing
Web and Mobile Application Security Assessment
Cloud Security Configuration and Architecture Review
Covers Internal as well as External Security Assessments
Realtime and tailored Security Assessment Activities Dashboard
Red Teaming and Social Engineering Attack Strategies
Complimentary Reassessment to ensure Vulnerabilities Closure
Breach and Cyber Attack Simulation to measure Cyber Resilience
Detailed Technical Recommendations Report for Vulnerability Mitigation
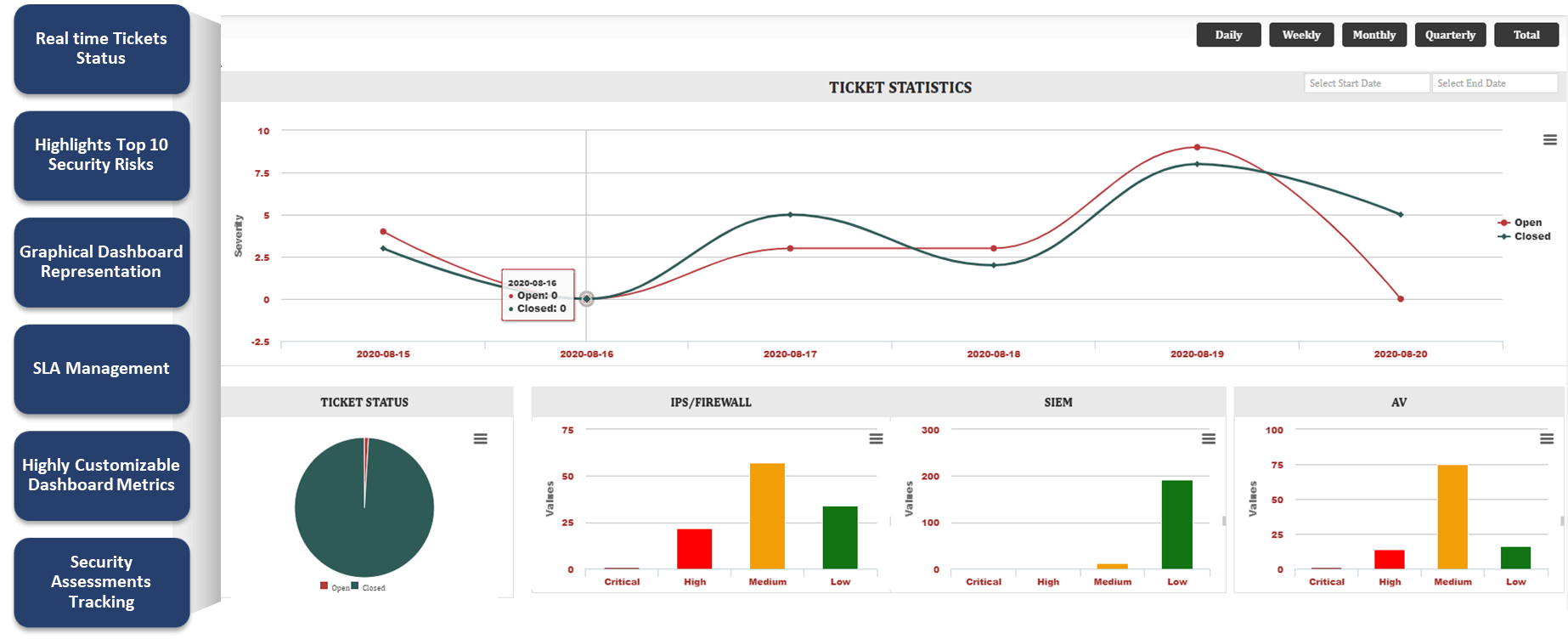
Varutra SOC & Global Threat Management Services Dashboard Application Our USP in SOC Offerings
Varutra SOCGTM delivers real time threat monitoring and alert analysis to minimize any impact on business operations and reduce overall security risk. By leveraging Varutra’s world-class analytics and network security services, organizations can improve business continuity and enhance the efficiency of their security operations, thus SOCGTM application adds value to the overall security operations program.
Why choose Varutra SOC & Global Threat Management Services?
Robust Security Posture
Monitor, Detect and Respond to attacks, identify malicious activities and stop unauthorized actions before it impacts business.
Proven Threat Mitigation
Our approaches are evolved over time and consistently evaluated by maintaining standard best practices to ensure customer network operations are as desired.
Real time Visibility
Our customizable “Varutra SOC & Global Threat Management Services Dashboard Application” provides real time insights of the security alerts Open/Closed at any given point of time.
Proactive Alert Validation
Our team is capable of intelligently analyzing the detected alert and proximately responds to such threats in order to remediate it.
Threat Detection & Response
We offer highly flexible Security Monitoring models (24X7, 9X6, etc.) as per the customer business needs. Our team ensures that round the clock threat reporting and mitigation is performed.
Actionable Deliverables
Customer IT Team is facilitated with real actionable reports and recommendations, trends identified in the infrastructure, to help improve the corporate security posture.
Security Advisory Services
Our team constantly monitors security vulnerabilities disclosed publicly which are mapped to customer technology base and are published with necessary actions to be undertaken.
Flexible Consulting Models
Our highly customizable offering model offers – offsite/onsite resource deployment model to utilize mission critical threats which requires immediate attention.
Cyber security managed SOC
Our Technology Partners
Cyber Attacks will Not Wait and so You Should Not. Talk to Our Sales Expert Now!
Prepare your organization to withstand from cyber security attacks and respond to most advanced threats
via our 24x7x365 proactive real time security monitoring.
We are here to help!