
Update added to bottom of the article.
Hackers are actively exploiting a zero-day vulnerability in Cleo managed file transfer software to breach corporate networks and conduct data theft attacks.
The flaw is found in the company's secure file transfer products, Cleo LexiCom, VLTrader, and Harmony, and is a flaw that allows unrestricted file upload and downloads that leads to remote code execution.
The Cleo MFT vulnerability affects versions 5.8.0.21 and earlier and is a bypass for a previously fixed flaw, CVE-2024-50623, which Cleo addressed in October 2024. However, the fix was incomplete, allowing threat actors to bypass it and continue to exploit it in attacks.
Cleo says its software is used by 4,000 companies worldwide, including TaylorMade, brother, New Balance, Hogan, Ryder, and Duraflame.
These attacks are reminiscent of previous Clop data theft attacks that exploited zero-days in managed file transfer products, including the 2023 mass-exploitation of MOVEit Transfer, the attacks using a GoAnywhere MFT zero-day, and the December 2020 zero-day exploitation of Accellion FTA servers.
However, cybersecurity expert Kevin Beaumont claims that these Cleo data theft attacks are linked to the new Termite ransomware gang, which recently breached Blue Yonder, a supply chain software provider used by many companies worldwide.
"Termite ransomware group operators (and maybe other groups) have a zero day exploit for Cleo LexiCom, VLTransfer, and Harmony," Beaumont posted to Mastodon.
In-the-wild attacks
The active exploitation of Cleo MFT software was first spotted by Huntress security researchers, who also published a proof of concept (PoC) exploit in a new write-up warning users to take urgent action.
"This vulnerability is being actively exploited in the wild and fully patched systems running 5.8.0.21 are still exploitable," explains Huntress.
"We strongly recommend you move any internet-exposed Cleo systems behind a firewall until a new patch is released."
Evidence of active exploitation of CVE-2024-50623 began on December 3, 2024, with a significant uptick in the volume of attacks observed on December 8.
Though attribution remains unclear, the attacks are linked to the following IP addresses in the United States, Canada, the Netherlands, Lithuania, and Moldova.
176.123.5.126 - AS 200019 (AlexHost SRL) - Moldova
5.149.249.226 - AS 59711 (HZ Hosting Ltd) - Netherlands
185.181.230.103 - AS 60602 (Inovare-Prim SRL) - Moldova
209.127.12.38 - AS 55286 (SERVER-MANIA / B2 Net Solutions Inc) - Canada
181.214.147.164 - AS 15440 (UAB Baltnetos komunikacijos) - Lithuania
192.119.99.42 - AS 54290 (HOSTWINDS LLC) - United States
The attacks exploit the Cleo flaw to write files named 'healthchecktemplate.txt' or 'healthcheck.txt' into the 'autorun' directory of the targeted endpoints, which are automatically processed by Cleo software.
When this happens, the files invoke built-in import functionalities to load additional payloads like ZIP files containing XML configurations ('main.xml'), which contain PowerShell commands that will be executed.
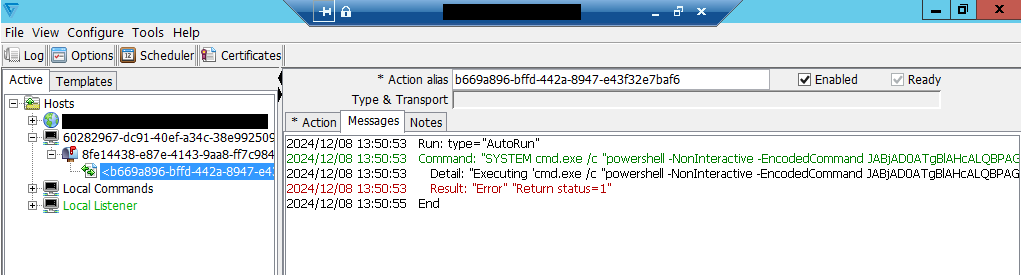
Source: Huntress
The PowerShell commands make callback connections to remote IP addresses, download additional JAR payloads, and wipe malicious files to hinder forensic investigation.
In the post-exploitation phase, Huntress says the attackers use 'nltest.exe' to enumerate Active Directory domains, deploy webshells for persistent remote access on compromised systems, and use TCP channels to ultimately steal data.
When done exploiting systems, the threat actors execute PowerShell commands to delete files from the attack, such as 'C:\LexiCom\cleo.1142.'
Huntress' telemetry indicates that these attacks have impacted at least ten organizations using Cleo software products, some of which do business in consumer products, the food industry, trucking, and shipping.
Huntress notes that there are more potential victims beyond its visibility, with Shodan internet scans returning 390 results for Cleo software products, The vast majority (298) of vulnerable servers are located in the United States.
Yutaka Sejiyama, a threat researcher at Macnica, told BleepingComputer that his scans return 379 results for Harmony, 124 for VLTrader, and 240 for LexiCom.
Action required
Given the active exploitation of CVE-2024-50623 and the ineffectiveness of the current patch (version 5.8.0.21), users must take immediate steps to mitigate the risk of compromise.
Huntress suggests moving internet-exposed systems behind a firewall and restricting external access to Cleo systems.
Companies can check if their Cleo servers were compromised by looking for suspicious TXT and XML files on the directories 'C:\LexiCom,' 'C:\VLTrader,' and 'C:\Harmony,' and inspect logs for PowerShell command execution.
Malicious XML files will be found in the 'hosts' folder and contain bash (on Linux) or PowerShell (on Windows) commands. Cleo has released scripts for both Linux and Windows that can help find these malicious XML files.
Finally, Huntress suggests removing any "Cleo####.jar" files, for example cleo.5264.jar or cleo.6597.jar) under the Harmony/VLTrader/Lexicom as they were likely uploaded during the exploitation of the vulnerability.
Also, it's recommended to turn off the autorun feature by following these steps:
- Open the Cleo application (LexiCom, VLTrader, or Harmony)
- Navigate to: Configure > Options > Other Pane
- Clear the field labeled Autorun Directory
- Save the changes
Huntress says Cleo expects a new security update for this flaw to be released later this week.
BleepingComputer asked Cleo additional questions about the vulnerability and was told the security update was "under development."
"We have identified a critical vulnerability in instances of Cleo Harmony, VLTrader, and LexiCom products," Cleo told BleepingComputer.
"Promptly upon discovering the vulnerability, we launched an investigation with the assistance of outside cybersecurity experts, notified customers of this issue and provided mitigation steps customers should immediately take to address the vulnerability while a patch is under development."
"Our investigation is ongoing. Customers are encouraged to check Cleo's security bulletin webpage regularly for updates. Cleo remains focused on supporting its customers and has extended enhanced 24/7 customer support services to those needing additional technical assistance in addressing this vulnerability."
BleepingComputer contacted Cleo again to see if there is a timeframe for when the security fix will be ready, but has not heard back.
Update 12/10/24: Added Cleo's statement and more technical information. Also fixed incorrect CVE in the beginning of the article.








Comments
chickenh00k - 4 weeks ago
This article provides valuable information about the ongoing exploitation of CVE-2024-50623 and the critical steps organizations need to take. It’s commendable that Huntress and Cleo have been proactive in offering mitigation advice and tools, but the situation highlights the importance of quicker patch development and communication during active vulnerabilities.
For affected users, following the recommended steps, such as reviewing logs, disabling autorun, and using Cleo's provided scripts, is crucial to minimize the risk. However, it’s equally important for organizations to implement long-term solutions like enhanced monitoring and restricting internet-exposed systems.
Hopefully, Cleo can expedite the release of a robust patch, as relying solely on mitigation steps poses a continued risk for many businesses. Organizations should also take this as a reminder to routinely evaluate their security posture and minimize exposure to vulnerabilities like this.
Looking forward to updates on Cleo’s patch timeline and any further recommendations.