Encrypting and Decrypting the Files Using GnuPG in Linux
Last Updated :
18 Jun, 2021
GnuPG is an encryption module that uses OpenPGP at its core. PGP stands for Pretty Good Privacy. It is an encryption program that provides authentication and cryptographic privacy for data communication. In the age where data is the new oil, the modern age thieves won’t intrude in through doors, windows or roofs, but instead, via wires and electrical signals in form of a few lines of code and commands. Nothing in this world is secure, which leads to an obvious conclusion that these thieves are inevitable.
But instead of trying to figure out which door these thieves will intrude through, we might just need to focus on what is it they need … Data. Data is the holy grail of wine which contains the ingredients of an individual’s social, financial, emotional, habitual and sometimes physical well-being. Encryption can serve as a solution to elude hackers, private organizations and government surveillance systems from monitoring your data. Encryption makes data useless to the person who does not possess a decryption key and useful to the one who does. If the key is lost, the data create remains locked forever.
Using GnuPG through Linux Terminal
We are assuming that you have installed GnuPG already. If not, go to GnuPG official website and download the required software and install it.
Encryption Process:
1. You can start the encryption process by generating a key.
gpg --gen-key
2. A name and an email address will later serve you like an easy way to remember your key rather than the long key-id.
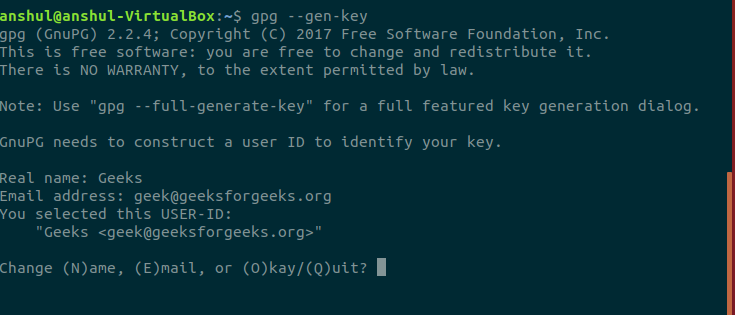
3. As soon as you choose okay a prompt for entering a passphrase will popup. This passphrase serves as a password for confirmation of the decryption key. It is a last line of defense for verification that the key belongs to you.
4. To see all the keys in your keyring, you can use the below command
$gpg --list-keys
5. Considering a file named sample.txt which is to be encrypted. For encrypting, use the below command
$gpg --output encryptionoutput.gpg --encrypt --recipient geek@geeksforgeeks.org sample.txt
Here, .gpg is an extension used for encrypted files.
Decryption Process:
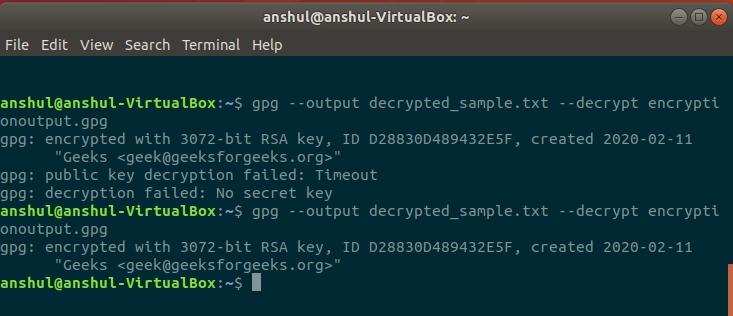
1. The encrypted file named encryptionoutput.gpg from the above given encryption process is to be sent to the recipient and in case you being the recipient, decryption is needed. Use the below command:
$gpg --output decrypted_sample.txt --decrypt encryptionoutput.gpg
2. Now it will ask you to enter the passphrase to unlock the OpenPGP secret key.
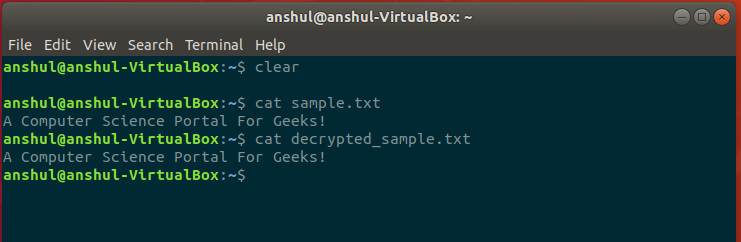
Now, you can check the result using ls command. The decryption process will only work if the private key has been imported into the keyring. You can also confirm the decryption by reading the content of the original file and decrypted file.
Important Points:
- Passphrase is needed for decryption, importing/exporting of private keys.
- GnuPG is user-specific as all other terminals programs i.e. if you run gpg as root then gpg will refer the root user keyring for further processes.
- Losing the private keys will result in a total loss of data encrypted via those keys and recovery will be impossible until the Quantum computers arrive and make the decryption math a child’s play.
Similar Reads
Encrypting and Decrypting the Files Using GnuPG in Linux
GnuPG is an encryption module that uses OpenPGP at its core. PGP stands for Pretty Good Privacy. It is an encryption program that provides authentication and cryptographic privacy for data communication. In the age where data is the new oil, the modern age thieves won't intrude in through doors, win
3 min read
Encrypt/Decrypt Files in Linux using Ccrypt
Ccrypt is a command line tool for encryption and decryption of data. Ccrypt is based on the Rijndael cipher, the same cipher used in the AES standard. On the other hand, in the AES standard, a 128-bit block size is used, whereas ccrypt uses a 256-bit block size. Ccrypt commonly uses the .cpt file ex
3 min read
Encrypt and Decrypt String File Using Java
In the field of cryptography, encryption is the process of turning plain text or information into ciphertext, or text that can only be deciphered by the intended recipient. A cipher is a term used to describe the encryption algorithm. It secures communication networks and aids in preventing illegal
3 min read
Encrypting Files Using vim editor in Linux
Vim, the popular text editor comes with a built-in feature to encrypt files with a password. Vim uses algorithms like Blowfish to encrypt files. It is faster and convenient than some other utilities available to do so. To get started, all you need is a system with a full version of vim installed. So
3 min read
Encrypt and Decrypt Using Rijndael Key in C#
To keep data secure and protected it is necessary to keep the data encrypted. As we know that in C# and in other languages too there are many ways for encrypting data. The Data Encryption Standard method used for encryption was not promising good security that led to the invention of a highly secure
7 min read
How to Setup Encrypted Filesystems and Swap Space Using ‘Cryptsetup’ Tool in Linux
An LFCE is in charge of the design, implementation, and continuous maintenance of the system architecture and is qualified and experienced to install, administer, and troubleshoot network services in Linux systems. Hard disc encryption for Linux Introduction to The Linux Foundation Certification Pro
4 min read
Blockchain - Encrypt & Decrypt Files With Password Using OpenSSL
Encryption is the process of encoding information or data in such a way that only authorized parties can access it. The process of encrypting information involves using a mathematical algorithm to transform the original information, known as plaintext, into a form that is unreadable to anyone who do
5 min read
How to Encrypt and Decrypt Text in Android Using Cryptography?
Cryptography is a technique of securing information and communications through the use of codes so that only those people for whom the information is intended can understand it and process it. Thus preventing unauthorized access to information. The prefix “crypt†means “hidden†and suffix graphy mea
14 min read
Automated Recursive Encryption in a Directory Using Shell Script
This script would encrypt file provided as an argument or a directory and its constituent files and sub-directories recursively. It would be very useful for automating the encryption of multiple files in a directory all together. How it works? If no arguments are given, throw an error and exit the p
3 min read
How to Copy Files and Directories in Linux | cp Command
In the world of Linux computers, a common and important job is copying files. The key tool for this task is the "cp" command. In this simple guide, we'll explore how to copy a file in Linux, looking at the basic steps, different choices you can make, and giving clear examples. We'll also take a peek
8 min read